In recent years, a brand new reconnaissance framework has become available to us that leverages many of the tools we are already using, but makes them far more powerful. This tool, Recon-ng, was developed by Tim Tomes while at Black Hills Information Security. He developed it as a Python script and tried to model its usage after Metasploit, making it easy for a pentester with Metasploit skills to use Recon-ng. It is built into Kali, so there's no need to download or install anything.
Let's explore its many and powerful capabilities a bit here.
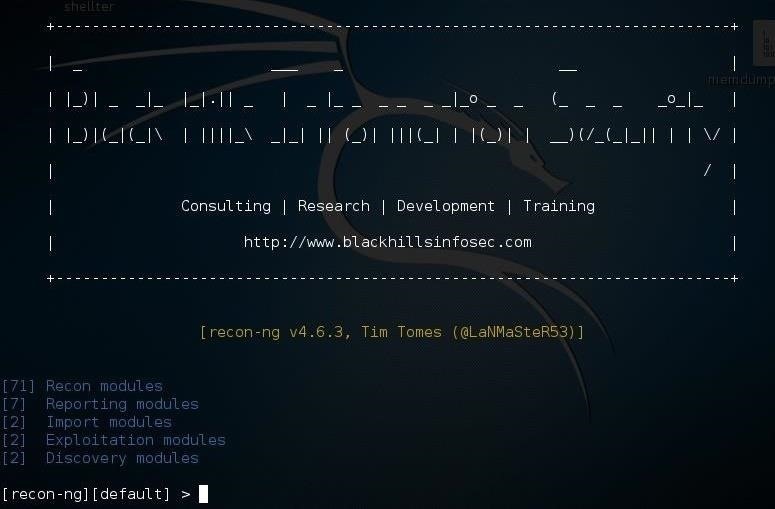
Step 1Starting Recon-Ng
Fire up Kali, open a terminal, and type:kali > recon-ng
Step 2Viewing Commands
At the prompt, let's type help in order to look at the commands we can use in Recon-ng.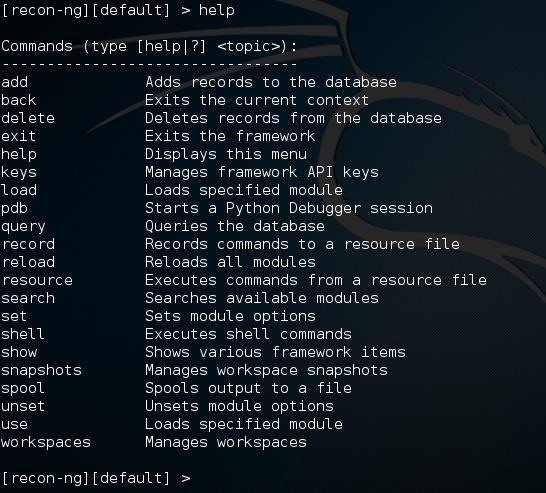
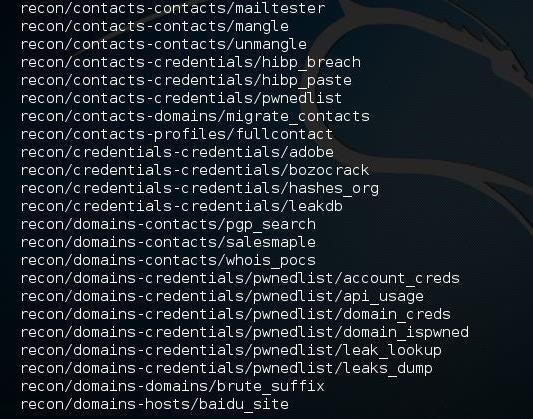
Step 3Showing Modules
To see all the modules in Recon-ng, we can type: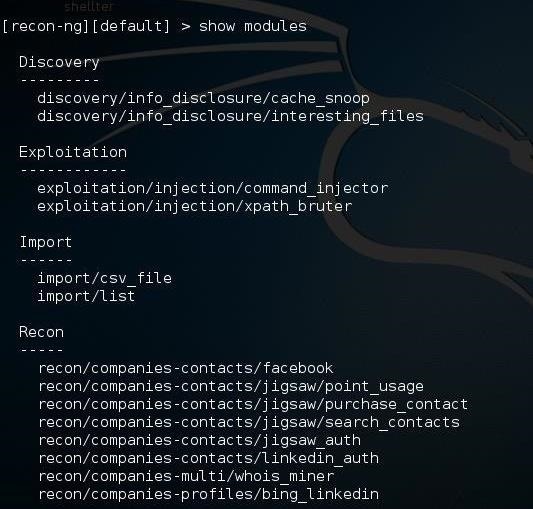
Step 4Viewing Keys
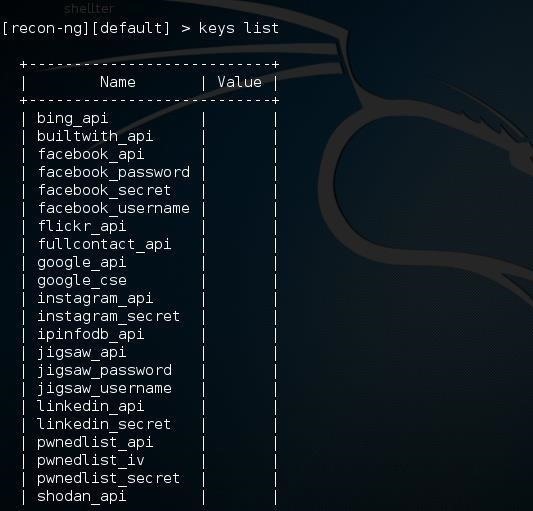
One of the strengths and beauties of Recon-ng is the use of various application programming interfaces (APIs) to extract useful recon information. For instance, Recon-ng can use Bing, Google, Facebook, Instagram, LinkedIn, and other online applications once you get the API key. With that key, you have almost unlimited access to that application.recon-ng > keys list
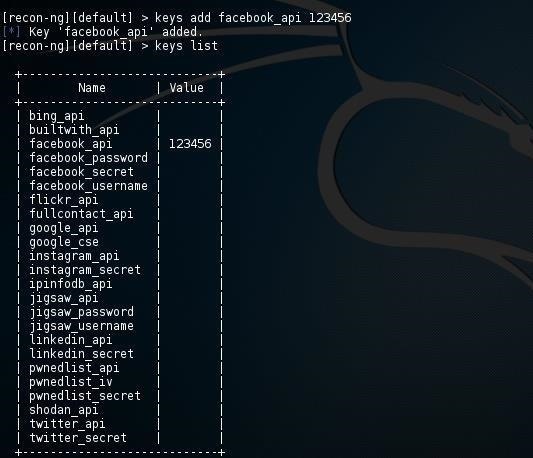
recon-ng > keys add facebook_api 123456
Now when you list the keys, you can see that your facebook_api key is listed. This means that when you use the Facebook recon module, it will automatically use this key to access Facebook like a Facebook application would.
Step 5Using Recon-Ng
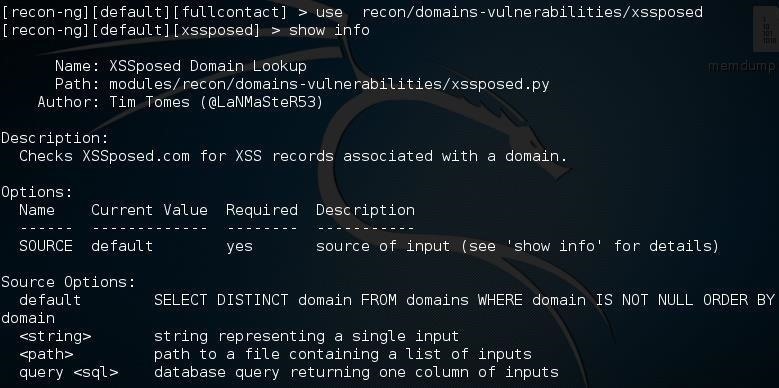
Now that we have explored a bit of Recon-ng, let's try using one the modules that does not require an API key. There are many, but let's use one for scanning for XSS (cross-site scripting) vulnerabilities called XSSposed. We can load this module by typing:recon-ng > use recon/domains-vulnerabilities/xssposed
This loads the module into memory and makes it ready for use. Let's get some info on this module by typing:
Note the similarity to Metasploit syntax.
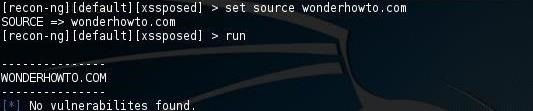
recon-ng > set source wonderhowto.com
Then tell Recon-ng to run:
Now, let's try scanning the website of the leading IT security training company in the U.S., SANS.org, which teaches many courses on website and web app security.
recon-ng > run
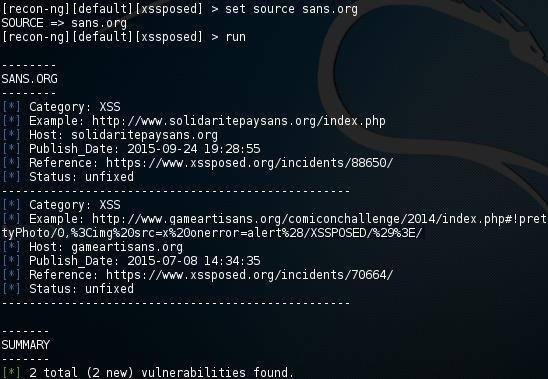
Recon-ng is one more tool in our hacker/pentester toolbox that provides us powerful capabilities for gathering necessary info on the target. In future tutorials in this series, we will explore its many varied capabilities, most particularly using APIs to garner key info on our target. So keep coming back, my novice hackers!
No comments:
Post a Comment